Cybersecurity Chronicles: Navigating the Digital Landscape of Fines, Bans, and Emerging Threats
‘Twas a beautiful morning ending the cold night.
The streets are so calm, there’s no soul in sight.
The air is so quiet, not a sound, not a peep.
So dark and heartwarming, is the coffee you sip.
On you way to the station, trees are covered in ice
And you can’t help but thinking: “Was I naughty or nice?”
But something you hear, as you walk down the alley:
A familiar sound coming from across the valley.
“Can it be?” you mutter with joy on your face,
You hold on to dear coffee as you quicken your pace.
You arrive at the platform; You calm your heart down.
You’d better believe it:
The Cybersecurity Express is coming to town!
Inside of your cabin, framed with green leaves and red beads
On shiny gloss paper, the schedule reads:
- Australia Will Fine Companies for Data Breaches
- Facebook Fined for Scrapped User Data
- FCC Bans the Use of Chinese Telecom Equipment
- Novel Wiper Found in Russia
Australia Will Fine Companies for Data Breaches
It is becoming even more expensive to not care about cybersecurity than to do so. Well, it wasn’t cheap to begin with, but now, in Australia, on top of the financial impact, the setbacks and the bad press you get from a data breach, you will also be fined by the state with up to 50 million dollars (Australian), 30% of the entity’s adjusted sale earnings in the related period (from when the breach occurred to when it was officially addressed), or three times the value of any benefit obtained through the misuse of information, whichever sum runs higher.
“Significant privacy breaches in recent months have shown existing safeguards are outdated and inadequate. These reforms make clear to companies that the penalty for a major data breach or repeated breaches, can no longer be regarded as the cost of doing business.” Attorney-General Mark Dreyfus states. Government officials said that the Privacy Legislation Amendment (Enforcement and Other Measures) Bill, as it is called, will also empower the Australian Information Commissioner to address security breaches more diligently, and hopefully make entities take cybersecurity more seriously.
This is the result of multiple major breaches that occurred lately, some examples being at Medibank that have resulted in the leak of personal information associated with 9.7 million customers, and at Optus with 2.1 million affected.
Facebook Fined for Scrapped User Data
If we are on the subject of companies getting fined for misuse of customer data, it’s hard not to talk about Facebook. The social media giant was fined, yet again, 275 million dollars (U.S.) by the Irish data protection commission (DPC) for not properly securing the mobile numbers, Facebook IDs, names, genders, locations, relationship statuses, occupations, dates of birth, and email addresses of no less than 533 million of its customers. That doesn’t strike as very sensitive data but considering the staggering number of impacted users and that it goes against GDPR regulations protecting the valued privacy of individuals, it’s not something that the Irish authorities could overlook. Facebook believes this data was extracted back in 2019 by abusing a flaw in its “Contact Importer” tool to associate phone numbers with a Facebook ID and then scraping the rest of the information to build a profile for the user. They also claim that the same year the bug was fixed, and the information just recently surfaced on the black market.
“There was a comprehensive inquiry process, including cooperation with all of the other data protection supervisory authorities within the E.U.,” reads the DPC announcement. While scraping is not hacking nor of illegal nature, the way the data sets collected by scrapers were combined with data from multiple points, creating complete profiles on users, marketable to threat actors so they can target said users with malicious campaigns, makes it the more serious. OSINT is information that is accessible via the open internet, but it easily falls into illegal grounds once it is weaponized to harm an individual.
FCC Bans the Use of Chinese Telecom Equipment
Back in August the Cybersecurity Express wrote about the investigation conducted by the FBI on whether Chinese-made networking equipment could pose a threat to U.S. national security. As a refresher you can read more about it here, but the marrow of the article was that an investigation led by the FBI determined the equipment could capture and disrupt highly restricted Defense Department communications, including those used by US Strategic Command, which oversees the country’s nuclear weapons. These accusations were not backed up by strong evidence and caused outrage among Chinese officials and manufacturers. On top of the communications capture issue, many of the cell towers that are owned by Chinese service providers have HD weather cameras and the FBI is certain that the feed is used by the Chinese to track strategical military movement.
Even though back in March 12, 2021 all these Chinese telecom and video surveillance companies were included in the List of Equipment and Services Covered By Section 2 of The Secure Networks act a final decision came when the U.S. Federal Communications Commission (FCC) formally announced it will no longer authorize electronic equipment from Huawei, ZTE, Hytera, Hikvision, and Dahua, deeming them an “unacceptable” national security threat. “The FCC is committed to protecting our national security by ensuring that untrustworthy communications equipment is not authorized for use within our borders, and we are continuing that work here,” FCC Chairwoman Jessica Rosenworcel officially stated.
It is not just the U.S. government getting rid of Chinese manufactured equipment, the U.K. has also banned the installation of visual surveillance systems procured in China on “sensitive” government sites. “Departments have been advised that no such equipment should be connected to departmental core networks and that they should consider whether they should remove and replace such equipment where it is deployed on sensitive sites rather than awaiting any scheduled upgrades,” U.K. officials said.
With almost all the electronics components and PCBs produced in China, it is hard to consider anything 100% safe. If this became unacceptable in the U.S., it is uncertain if it will spill into N.A.T.O. states as the norm, or if it will serve as an example for the E.U. which is trying cut its dependencies from communist states.
Novel Wiper Found in Russia
According to researchers at Kaspersky a wiper disguised as ransomware is permanently destroying data in Russian courts and city hall offices. The never-before-seen CryWiper, named after the extension .cry that gets appended to destroyed files, seems to be targeting it’s victims. Wipers disguised as ransomware are not something new, but they have become more common in the past few years, with known examples like: NotPetya, DoubleZero, IsaacWiper, HermeticWiper, CaddyWiper, WhisperGate and others.
CryWiper has some similarities with IsaacWiper, which targeted organizations in Ukraine. It would be ironic for it to be a modified version of it made to strike back. Both wipers use the same algorithm for generating pseudo-random numbers that go on to corrupt targeted files by overwriting the data inside of them. It uses Mersenne Vortex PRNG, an algorithm that is rarely seen in the wild, making this detail something that stood out to the researchers. CryWiper also has the same email address in the ransom note as other ransomware families known as Trojan-Ransom.Win32.Xorist and Trojan-Ransom.MSIL.Agent. The CryWiper sample Kaspersky analyzed is a 64-bit executable file for Windows. It was written in C++ and compiled using the MinGW-w64 toolkit and the GCC compiler.
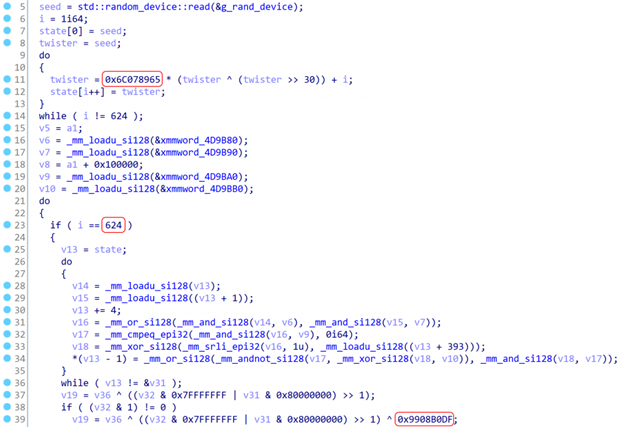
“In many cases, wiper and ransomware incidents are caused by insufficient network security, and it is the strengthening of protection that should be paid attention to. We assume that the number of cyberattacks, including those using wipers, will grow, largely due to the unstable situation in the world.” stated the researchers at Kaspersky.
This has been quite the ride on CyBourn’s Cybersecurity Express that really puts some things into perspective. The uncertain nature of tomorrow creates the need for innovation, to find better and safer alternatives for the days to come. Hope you enjoyed the ride. We look forward to seeing you aboard next time!