Cybersecurity Dispatch: From DDoS Defense to 5G Security and Global Threat Insights
It’s been a while since you heard the Cybersecurity Express whistling in the distance! We’ve been busy, but so have the hackers as they hacked, computers as they crunched and the routers as they routed. Ah, such is the IT world, it never slumbers. Climb aboard, have a seat, get comfy, as we are handing out today’s schedule:
- Cloudflare Defends Minecraft Against DDoS.
- 17-year-old to blame for GTA 6 and Uber Hack?
- Ferrari was not fast enough for the hackers!
- FiGHT™ for reliable access of 5G networks.
- NSA, CISA, FBI Reveal Top Exploited CVEs.
Cloudflare Defends Minecraft Against DDoS.
A multi-vector attack targeted Wynncraft, with a 2.5 Tbps DDoS (distributed denial-of-service) according to Cloudflare, the web app security giant. Among the largest Minecraft servers, Wynncraft was under siege for about two minutes with a flood of UDP and TCP packets aiming to keep hundreds of thousands of players out of the server. Fortunately, this DDoS was mitigated, and it is reportedly the biggest prevented DDoS we’ve seen so far.
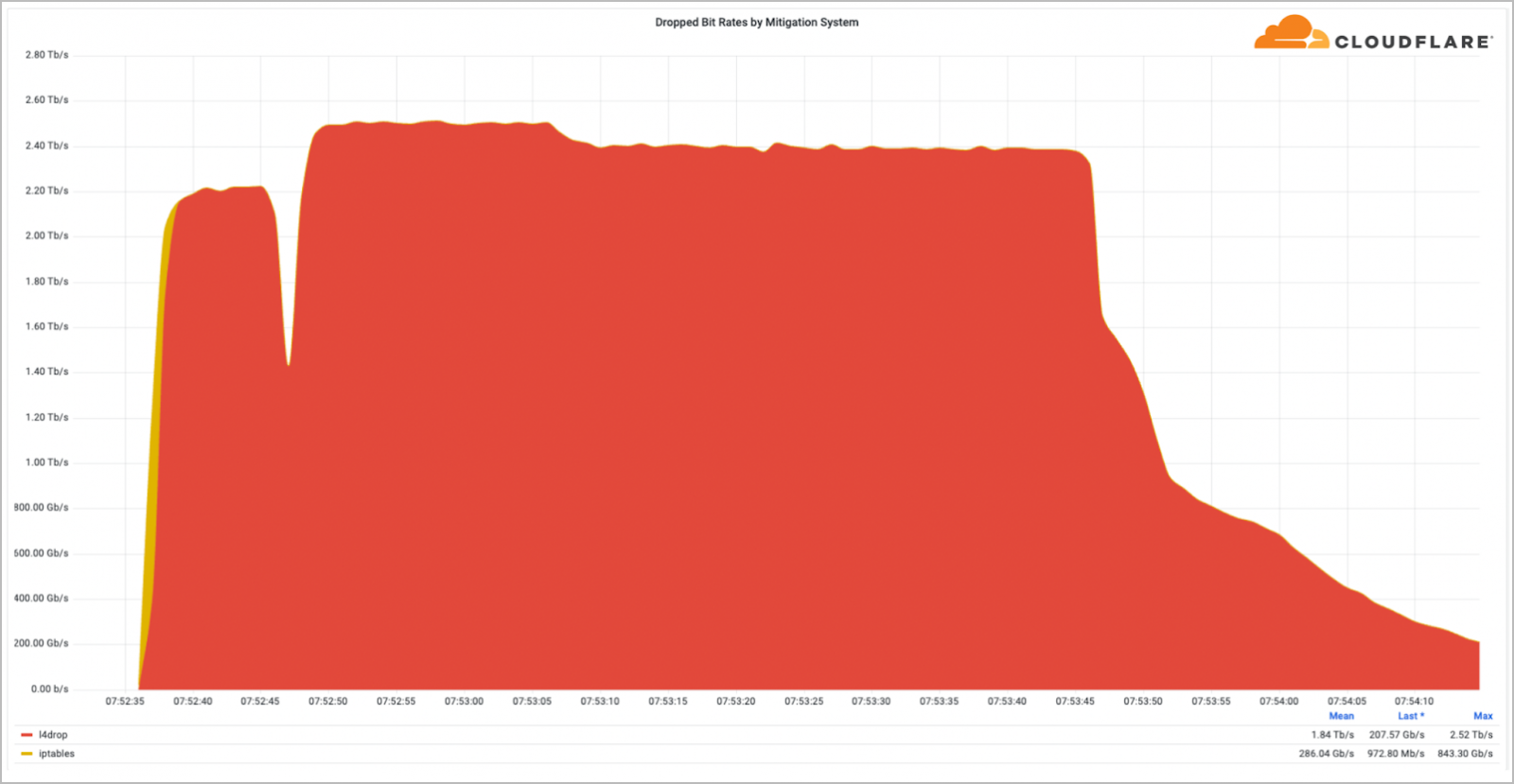
This is an example of a layer 3 and 4 attack, trends indicating a steady increase to almost double per yearly basis, with this year’s occurrence spiking by 97% compared to last year’s, and we see a 405% increase if we are comparing to Q2 2022. These types of DDoS attacks are mainly targeting the gaming industry and are due to the observed Mirai comeback that is abusing IoT technology, a subject that we previously covered. But the biggest increase of any DDoS technique is the abuse of the BitTorrent protocol, reaching a staggering 1,200% when compared to the previous quarter. “A malicious actor can spoof the victim’s IP address as a seeder IP address within [BitTorrent] Trackers and DHT (Distributed Hash Tables) systems, then clients would request the files from those IPs. Given a sufficient number of clients requesting the file, it can flood the victim with more traffic than it can handle.” Cloudflare stated.
17-year-old to blame for GTA 6 and Uber Hack?
On September 22, the City of London police detained a 17-year-old in connection with the hacks of Uber and Rockstar Games, the creator of the famous Grand Theft Auto franchise.
According to The Desk, the teenager is being detained on suspicion of conspiring on assaulting at least two distinct computer systems. It all started when someone under the alias “teapotuberhacker” released 90 videos of gameplay to the GTA Forums, more than 50 hours of game content, that confirmed a lot of suspicions held by the fans. By threatening to leak the GTA V and GTA VI source code, the hacker appeared to be blackmailing Rockstar Games for ransom. The public disclosure of the source code would leave GTA V and GTA VI vulnerable to hacking and other kinds of exploitation. Rockstar Games had issued takedown requests on social media and had tweeted acknowledging that they had “suffered a network intrusion.”, stating that they were “very saddened” by the event but assured that development on the game will proceed according to schedule.
The same user claimed responsibility for the very famous Uber data breach that occurred on Sep 15 2022. As The Guardian wrote, both hacks were possible due to the abuse of a Slack vulnerability. It’s believed that the 17-year-old is affiliated with “Laspus$” a group of hackers suspected of involvement in other high-profile hacks at companies like Cisco, Microsoft, Okta, Samsung, and Uber since 2021. The arrest was the result of a joint investigation by the FBI and the UK’s Cyber Crime Unit.
Ferrari was not fast enough for the hackers
It appears that 7GB of data from the Ferrari website was leaked and published on the dark-web page run by ”RansomEXX” group, seemingly containing internal paperwork, datasheets, repair guides, and other sensitive materials. A private document can be seen in a screenshot taken from the stolen data. It appears to be a purchase contract for a certain Ferrari brand automobile.

This is the second time Ferrari is hacked this year alone, now happening not one week after Romanian firm Bitdefender became the official sponsor of Ferrari’s Formula One team. Just bad timing, I guess…
The Italian manufacturing firm Speroni was attacked by the Everest cyber gang in December 2021. Threat actors promoted the theft of 900 GB of Speroni data, which contained private information about the company’s partners, including Ferrari, Lamborghini, Fiat Group, and other Italian automakers. Not so long ago threat actors also took advantage of Ferraris announcement that it will produce NFTs based on Ferrari automobiles and hijacked the company’s subdomain, using it to host a fake NFT sellout event.
Ferrari confirmed that some internal documents had been posted online and that they are working to identify how this had happened but Is denying that any breach took place or that there was a ransom involved.
FiGHT™ for reliable access of 5G networks
A joint effort of MITRE and the Department of Defense (DoD) concluded with the launch of FiGHT (5G Hierarchy of Threats) adversarial threat model for 5G systems, an unprecedented freely available platform empowering organizations to reliably assess the confidentiality, integrity, and availability of 5G networks, as well as the devices and applications using them.
“We’re honored to join the Department of Defense in equipping the 5G community with a collaborative, open-source tool against cyber threats. FiGHT helps stakeholders assess where cyber investments should be made to achieve the highest impact as they build, configure, and deploy secure and resilient 5G systems.” said Charles Clancy, Ph.D., senior vice president at MITRE Labs.
Derived from the industry standard MITRE ATT&CK®, FiGHT is a purpose-built model of observed adversary behaviors in telecommunications environments. It serves as a foundation to 5G security research and can be used in various ways:
- conduct threat assessments
- identify coverage gaps
- enable adversarial emulation
- inform cyber investment planning.
NSA, CISA, FBI Reveal Top Exploited CVEs
National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) compiled a report on the “Top Common Vulnerabilities and Exposures (CVEs) Actively Exploited by People’s Republic of China State-Sponsored Cyber Actors” since 2020. The report highlights how PCR threat groups continuously abuse known vulnerabilities to breach networks and keep a foothold. There exploits pose a significant risk to Information Technology Sector organizations (including telecommunications providers), Defense Industrial Base (DIB) Sector organizations, and other critical infrastructure organizations. Everything listed in the report is no news, they are public CVEs and almost all of them are mitigated through patching. We cannot put a bog enough emphasis on this: Always patch as soon as a patch is made available!
All good things must come to an end, and so does this journey aboard CyBourn’s Cybersecurity Express. We don’t know exactly when the train will depart again, but we know it will be soon and no one will be left behind.
Hope you enjoyed the ride. We look forward to seeing you aboard next time!