The Cybersecurity Express – 21 June 2022
You’ve been waiting on the platform for far too long, perhaps beginning to wonder if the train will ever arrive… But you waited, you endured, and your patience is about to pay off! From the depot, you hear a familiar sound: the Cybersecurity Express awakens from its slumber! You are happy to be back on board and eagerly await the journey ahead. The schedule reads:
- First stop: Study shows that small businesses aren’t ready for a cyber attack.
- It didn’t really take for a study to know that…
- Second stop: Quantum computing means doom for cybersecurity as we know it.
- Third stop: Apple’s M1 chip has a vulnerability that cannot be patched.
Small Businesses Aren’t Ready for a Cyber Attack
It may not come as a surprise, but first stop brings news that most small businesses haven’t even considered cybersecurity. CNBC conducted a quarterly survey involving more than 2000 small US business owners to understand their overall business environment along with their own business’s health. The latest one shows that only 5% of the owners feel that cyber threats are the biggest risk to their business. This percentage is steadily maintained over the quarterly studies, and not growing, despite the current instability caused by Russian latest cyber attacks that took place all over the world and the warnings issued by the US government. It seems inflation is the most perceived threat to the business, a perception that has grown from 31% to 38% in one quarter alone. Now that COVID-19 and supply chain fear is dwindling, it appears that cybersecurity is once again shadowed by a new threat.
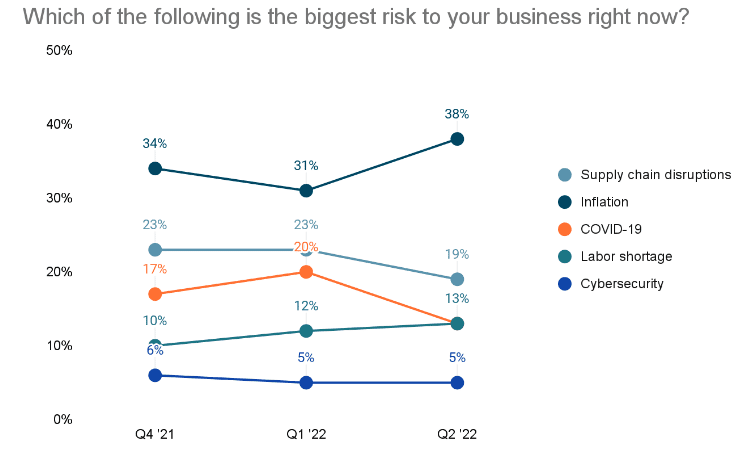
CNBC|SurveyMonkey Small Business Survey Q2 2022
What adds salt to the wound is that most of those who are not even concerned with cybersecurity believe they can successfully respond to/mitigate a successful cyber attack on their own. The numbers only get worse: Less than half or the owners surveyed have installed antivirus or malware software, strengthened their passwords, or backed up files on an external hard drive to protect their business against potential cyber attacks. Only a third each have enabled automatic software updates or enabled multi-factor authentication. Just one quarter have installed a virtual private network (VPN).
Unfortunately, cyber attacks fall in the category of “intangible” threats, for most people, which are easily overlooked for a more “palpable” concern, but the damage done by cyber crime is real nonetheless and, even a partially successful attack, can have lasting consequences, with financial impact or staining the company image irreversibly. Truth be told, for a small business, the cost associated with cybersecurity is something that makes it difficult to implement, but luckily cybersecurity is being made more affordable by companies like CyBourn, who offer cost effective solutions, tailored for small and medium businesses.
Quantum Computing: An Emerging Threat for Cryptography
Quantum Computing is threatening the strength of our encryption and cryptographic mechanisms, as it becomes less science-fiction and more science-fact. Although still experimental and with hardware taking up huge spaces, we must not forget that, not so long ago, so were the computers we you are now reading this article from.
As quantum computing is becoming a reality, one question becomes more prevalent:
“Will we be ready for a quantum based cyber attack?”
It is not a question of “if”, because it is certain, that’s why U.S. Special Operations Command is worried about this future threat and why it’s planning ahead in this very matter. But why is a quantum computer such a big threat? It all comes down to speed. Every encryption mechanism that we use now can be decrypted, given enough time or computing power. Trying to sum up what a quantum computer is, in just a short paragraph, is in its self a task for such a computer, but we’ll give you a gross simplification: Instead of relying on the processing potential of the bit, which can have only two values of 1 or 0, this new breed of computers uses a qubit (quantum bit) which can be either 1, 0 or both, which can be looked at as a 3rd state of the bit. This is possible by exploiting the superposition property of subatomic particles. So, if you have two qubits, you have the information of 00 11 10 01, all at the same time. The computing power increasing exponentially with every qubit you add. It is hard to get a precise estimate, but it is said a quantum computer could do in four minutes what it would take a traditional supercomputer 10,000 years to accomplish, for the same number of bits/qubits. This means that a quantum computer does not have to wait for one process to end before it can begin another, it can compute them at the same time.
Returning to the cybersecurity aspect, because we are not quantum scientists, this would mean that a decryption could be handled in minutes, not centuries, and that will pose a huge threat to everything that uses encryption: passwords, private data storage, cryptocurrency, you name it! But’ perhaps we are giving the quantum computer a bad rep by only talking about the harm it can do. Such a powerful tool is intended for good use and can bring huge advances in many fields by taking machine learning and neural networks to a whole new level, it can optimize energy and fuel consumption and solve humanity’s biggest threats like global warming. It’s potential to do good, more than justifies the possible use for harm, because with great power comes great responsibility! Where have we heard that before?…
The quantum computers that we have now, are far from these performance levels, and still must battle qubit growth stability, interference, and many other quirks before it becomes usable, but it is good to plan ahead for a safe and organic introduction of this technology when its time arrives.
Apple’s M1 chip hardware vulnerability
Researchers at MIT have created a new type of attack, which bypasses pointer authentication codes (PAC) with a combination of memory corruption and speculative execution techniques. The attack shows that pointer authentication can be fooled without leaving a trace, and, as it utilizes a hardware mechanism, no software patch can fix it.
Named “PACman”, (no one saw that coming) works by “guessing” a cryptographic signature issued by the PAC that confirms an app hasn’t been maliciously altered. This is done using speculative execution — an optimization technique in which a processor performs a series of speculated tasks before it is prompted to, in order to speed things up — to try all PAC verification results against a hardware side-channel that reveals whether or not the guess was correct, which can be done because they are only a “handful” PAC verification codes. In a proof of concept, it was shown that the attack works against the kernel which has a “massive implications for future security work on all ARM systems with pointer authentication enabled” says Joseph Ravichandran, a PhD student at MIT CSAIL and co-lead author of the research paper. Apple has implemented pointer authentication on all its custom ARM-based silicon so far, including the M1, M1 Pro and M1 Max. Several other chip manufacturers, including Qualcomm and Samsung, are about to manufacture chips supporting the hardware-level security feature. The attack was not yet tested on Apple’s unreleased M.2 chip, which also uses the infamous module.
A note to make here is that the Pacman attack isn’t a “magic bypass” for all security on the M1 chip and can only take on an existing bug that pointer authentication protects against. The same is confirmed by Apple engineers, which “concluded this issue does not pose an immediate risk to the users and is insufficient to bypass operating system security protections on its own.”
This has been a fun ride on CyBourn’s Cybersecurity Express that really puts some things into perspective. Do not worry about the uncertain nature of tomorrow as it creates the need for innovation, and it drives us further. Hope you enjoyed the ride. We look forward to seeing you aboard next time!